Most Cisco AnyConnect VPN configurations I see in the field, or have deployment myself, are terminated on a Cisco ASA firewall who is directly connected to the internet. However, in some bigger networks it is not uncommon to have another firewall in front of the remote access / VPN block in your network or to have an access-list on the routers in the internet edge.
Everybody knows the story about the biggest pro which the Cisco AnyConnect solution has if you compare it to the old IPSEC remote access based solution –> “it just works everywhere™”. That story is based on the fact that in most guest and mobile networks SSL network traffic (TCP/443) is allowed. This is true; AnyConnect will work fine if DNS is working and TCP port 443 is open. However, AnyConnect will try to use the DTLS protocol first which uses UDP port 443, if it fails than the client will fall back to use SSL for the transport of user data. The reason that AnyConnect prefers DTLS is that DTLS has less delay because of the connectionless nature of UDP and thus performance is better then with a SSL tunnel.

It is very easy to check if you are actually using DTLS in the AnyConnect client:
Conclusion:
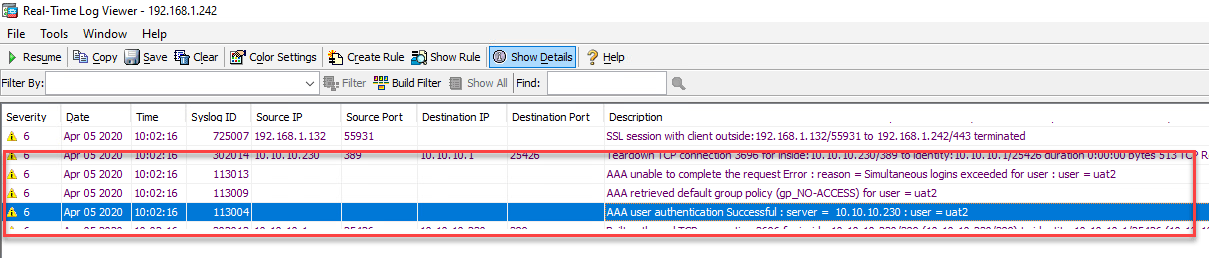
If you filter the network traffic destinate to a Cisco IOS webvpn router or Cisco ASA firewall in the remote access / VPN block in your network don’t forget to open UDP port 443 also.. 🙂

Cisco Anyconnect Ports Firewall
Cisco Anyconnect Port 80
Example Console Port Labeled CONSOLE (Cisco 1811W Router) If you need help locating the console port on your router, refer to the router documentation. If you are using the ATEN USB Serial Adapter with Mac OS X Lion, there are known issues with getting the adapter to work correctly. Contact Cisco dCloud Support for assistance. Under source, use the IP range for Anyconnect, Destination IP to the RDP Server and Destination port to 3389. That will tell you if there is any policy in place to block the traffic, in particular to RDP (TCP/3389) Was this post helpful?
